Threat Hunting - Simplifying The Beacon Analysis Process - Active Countermeasures
By A Mystery Man Writer
Description
Simplifying Beacon Analysis through Big Data Analysis - Active Countermeasures

Closer Look at Threatsys' Cybersecurity Expertise in Fortifying Financial Technology, Threatsys, Eradicating Threats Globally, Global Cyber Security Provider

What is Threat Hunting? Threat Hunting Types and Techniques

Home - Active Countermeasures

The Automotive Threat Modeling Template, NCC Group Research Blog
Beacon Analysis - The Key to Cyber Threat Hunting - Active Countermeasures

How to Threat Hunt for C2 Traffic Regardless of Protocol or Port
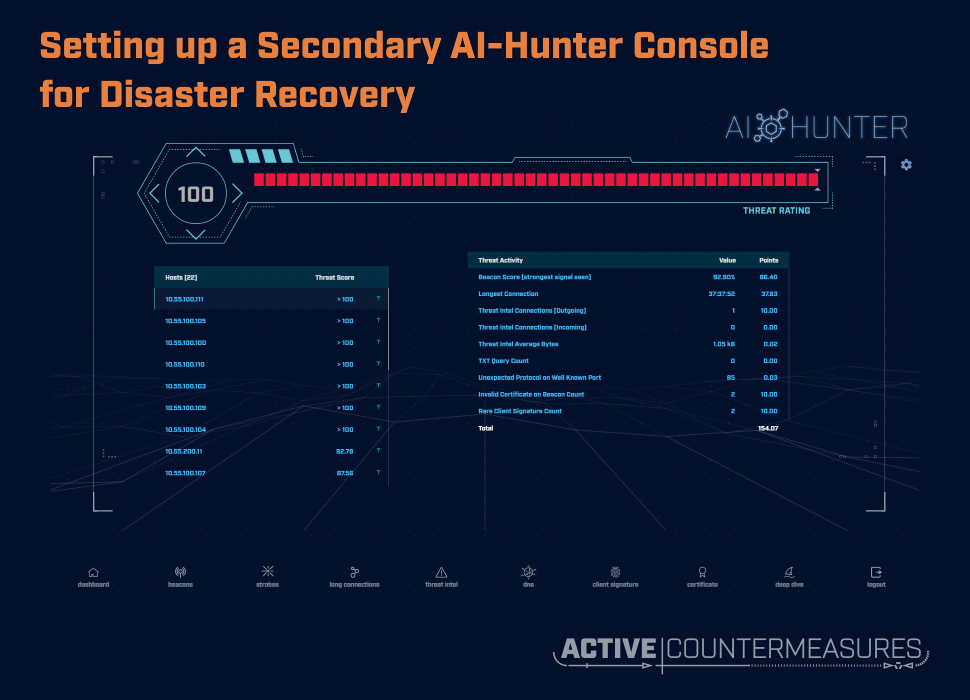
Threat Simulator - Active Countermeasures
Even More on Threat Hunting
Threat Hunting - Simplifying The Beacon Analysis Process - Active Countermeasures

About Us - Active Countermeasures
Detecting Beaconing Attacks by Advanced Threat Hunting
from
per adult (price varies by group size)







